“Hello pervert, l’ve sent this message from your iCloud mail” scam (scam) - Free Instructions
“Hello pervert, l’ve sent this message from your iCloud mail” scam Removal Guide
What is “Hello pervert, l’ve sent this message from your iCloud mail” scam?
“Hello pervert, l've sent this message from your iCloud mail” is an email scam that attempts to extort money from you
By referencing Pegasus, the scammer uses a real and widely-feared piece of spyware to add credibility to their claims. However, in reality, installing such spyware on multiple devices is highly unlikely without physical access or severe security lapses on the victim's part.
Next, the email mentions that the scammer has recorded compromising videos of the victim engaging in private activities. This is a common psychological trick used in extortion scams known as sextortion. The scammer relies on the victim's fear and embarrassment, suggesting that these videos will be shared with all of their contacts, including friends, family, and colleagues. This threat is designed to push the victim into complying with the scammer's demands out of panic and shame.
To further manipulate the victim, the scammer sets a strict deadline, usually 48 hours, to make the payment in cryptocurrency. The use of cryptocurrency, such as Litecoin, adds another layer of intimidation because it is often perceived as complex and untraceable.
The email author reassures the victim that their privacy will be restored once the payment is made, claiming they will delete the videos and remove the spyware. This promise is entirely false, as scammers rarely follow through on their promises even after receiving payment.
The email also contains warnings against seeking help or taking any actions to protect oneself. The scammer advises against contacting the police, destroying devices, or attempting to reset accounts, claiming they are monitoring all activity and will immediately release the videos if they detect such actions. These threats are baseless, as most scammers do not have the technical capability to monitor devices in real time.
In reality, the claims made by the scammer are almost always false. They rely on the psychological impact of their threats rather than any actual evidence or technical ability. The goal is to create a sense of urgency and helplessness, making the victim feel that paying the ransom is the only way to avoid public humiliation.
Here's the full email message you might receive one day:
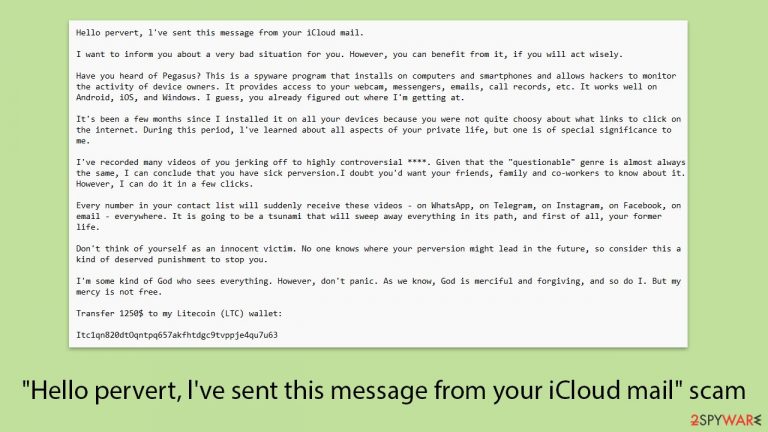
Hello pervert, l've sent this message from your iCloud mail.
I want to inform you about a very bad situation for you. However, you can benefit from it, if you will act wisely.
Have you heard of Pegasus? This is a spyware program that installs on computers and smartphones and allows hackers to monitor the activity of device owners. It provides access to your webcam, messengers, emails, call records, etc. It works well on Android, iOS, and Windows. I guess, you already figured out where I'm getting at.
It's been a few months since I installed it on all your devices because you were not quite choosy about what links to click on the internet. During this period, l've learned about all aspects of your private life, but one is of special significance to me.
I've recorded many videos of you jerking off to highly controversial ****. Given that the “questionable” genre is almost always the same, I can conclude that you have sick perversion.I doubt you'd want your friends, family and co-workers to know about it. However, I can do it in a few clicks.
Every number in your contact list will suddenly receive these videos – on WhatsApp, on Telegram, on Instagram, on Facebook, on email – everywhere. It is going to be a tsunami that will sweep away everything in its path, and first of all, your former life.
Don't think of yourself as an innocent victim. No one knows where your perversion might lead in the future, so consider this a kind of deserved punishment to stop you.
I'm some kind of God who sees everything. However, don't panic. As we know, God is merciful and forgiving, and so do I. But my mercy is not free.
Transfer 1250$ to my Litecoin (LTC) wallet:
Itc1qn820dtOqntpq657akfhtdgc9tvppje4qu7u63
Once I receive confirmation of the transaction, I will permanently delete all videos compromising you, uninstall Pegasus from all of your devices, and disappear from your life. You can be sure – my benefit is only money. Otherwise, I wouldn't be writing to you, but destroy your life without a word in a second.
I'll be notified when you open my email, and from that moment you have exactly 48 hours to send the money. If cryptocurrencies are unchartered waters for you, don't worry, it's very simple. Just google “crypto exchange” or “buy Litecoin” and then it will be no harder than buying some useless stuff on Amazon.Itc1qn820dtOqntpq657akfhtdgc9tvppje4qu7u63
Once I receive confirmation of the transaction, I will permanently delete all videos compromising you, uninstall Pegasus from all of your devices, and disappear from your life. You can be sure – my benefit is only money. Otherwise, I wouldn't be writing to you, but destroy your life without a word in a second.
I'll be notified when you open my email, and from that moment you have exactly 48 hours to send the money. If cryptocurrencies are unchartered waters for you, don't worry, it's very simple. Just google “crypto exchange” or “buy Litecoin” and then it will be no harder than buying some useless stuff on Amazon.
I strongly warn you against the following:
- Do not reply to this email. I've sent it from your iCloud mail.
- Do not contact the police. I have access to all your devices, and as soon as I find out you ran to the cops, videos will be published.
- Don't try to reset or destroy your devices. As I mentioned above: I'm monitoring all your activity, so you either agree to my terms or the videos are published.
Also, don't forget that cryptocurrencies are anonymous, so it's impossible to identify me using the provided address.
Good luck, my perverted friend. I hope this is the last time we hear from each other.
And some friendly advice: from now on, don't be so careless about your online security.
Scammers often acquire email addresses through various methods such as data breaches, purchasing lists on the dark web, or using automated software to scrape the internet for contact information. These large pools of email addresses allow scammers to cast a wide net, increasing their chances of finding someone who will respond out of fear or confusion.
While most email filters are designed to catch and quarantine such scam attempts, these filters can sometimes be bypassed. Scammers constantly refine their techniques to evade detection by using unpredictable email formats and engaging subject lines that provoke curiosity or urgency.
This increases the likelihood that their message will reach your primary inbox rather than being relegated to the spam folder. By invoking the name of sophisticated malware like Pegasus, scammers exploit a general lack of detailed technical knowledge among the public, making their threats seem more credible and urgent.
Steps to take after receiving the “Hello pervert, l've sent this message from your iCloud mail” scam message
If you come across an email like this, the most important thing is to stay calm. Avoid replying to the email or making any payments, as this only confirms to the scammers that your email is active and you might be susceptible to future scams.
The best course of action is to report the email to your local law enforcement or a cybercrime agency. Sharing details about the email can assist authorities in tracking down and addressing these kinds of cyber threats. Providing comprehensive information will aid their investigation.
To protect your devices, conduct a thorough scan using up-to-date antivirus software such as SpyHunter 5Combo Cleaner or Malwarebytes to check for any malicious programs, even though it’s highly unlikely that the threats mentioned in the email are real. Ensuring your devices are clean is a good precautionary measure.
If you have already sent money, it is crucial to contact your bank right away to report the fraud and explore options for recovering the funds. Additionally, change your passwords, especially for your email account, and enable multi-factor authentication to add an extra layer of security. This helps prevent unauthorized access and enhances overall protection.
How to prevent from getting malware
Protect your privacy – employ a VPN
There are several ways how to make your online time more private – you can access an incognito tab. However, there is no secret that even in this mode, you are tracked for advertising purposes. There is a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
No backups? No problem. Use a data recovery tool
If you wonder how data loss can occur, you should not look any further for answers – human errors, malware attacks, hardware failures, power cuts, natural disasters, or even simple negligence. In some cases, lost files are extremely important, and many straight out panic when such an unfortunate course of events happen. Due to this, you should always ensure that you prepare proper data backups on a regular basis.
If you were caught by surprise and did not have any backups to restore your files from, not everything is lost. Data Recovery Pro is one of the leading file recovery solutions you can find on the market – it is likely to restore even lost emails or data located on an external device.
