LAZPARKING ransomware (Virus Removal Guide) - Recovery Instructions Included
LAZPARKING virus Removal Guide
What is LAZPARKING ransomware?
LAZPARKING ransomware – a file-locking computer virus that is aimed at companies
LAZPARKING ransomware is a cryptovirus that encrypts all non-system files on a targeted computer (or a whole network) and then tries to extort money for a decryption tool. This particular file-locking parasite is aimed at companies, but that doesn't mean that everyday computer users are safe.
When the ransomware virus finds its way into a computer, it encrypts all personal (or company) files like documents, backups, pictures, archives, databases, and so on. During the encryption process, all files are appended with a .LAZPARKING-xxxxxxxxxx extension.
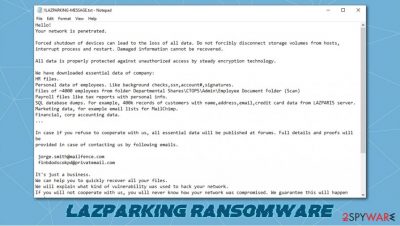
Like all ransomware, including Fair, Weui, or LANDSLIDE, after the encryption, .LAZPARKING virus generates a ransom demanding note. This note, titled !!LAZPARKING-MESSAGE.txt is placed in all contaminated folders. But unlike other ransomware, victims of this cryptovirus receive personalized ransom notes.
| name | LAZPARKING ransomware, .LAZPARKING file virus |
|---|---|
| type | Ransomware |
| Appended file extension | All non-system files receive a .LAZPARKING-(random characters) extension |
| Ransom note | !!LAZPARKING-MESSAGE.txt |
| Additional information | Before encryption, cybercriminals steal a lot of sensitive company data and treated to release it to the public if the ransom demands aren't met |
| Criminal contact details | Victims can reach hackers by two given emails – jorge.smith@mailfence.com and finbdodscokpd@privatemail.com |
| Malware removal | Instead of dealing with the criminals, victims should remove the infection with powerful anti-malware software and look for alternative data recovery options |
| System fix | Computer systems that suffer from cyberattacks have their system files and settings messed up, to revert any changes, use the FortectIntego tool after ransomware elimination |
The first part of the LAZPARKING ransomware ransom demanding note consists of warnings. Hackers state that the victim network was penetrated and that any forced system shutdowns or storage volume disconnections might lead to data being damaged thus unrecoverable.
Then the creators of LAZPARKING ransomware point out that they have stolen the following data of the company:
- Approximately 4,000 files on company employees
- Payroll files with personal information
- Four hundred thousand customer records, including their names, addresses, credit card info, etc.
- Marketing data
- Financial, accounting data
If victims of LAZPARKING ransomware will refuse to cooperate with the cybercriminals, they threaten to make this stolen data available to the general public. They promise to provide proof of their actions when the victims contact them by either one of two given emails – jorge.smith@mailfence.com and finbdodscokpd@privatemail.com.
In the last part of the LAZPARKING virus note, the criminals try to convince their victims to pay for the decryption tool by stating that they will explain how they hacked the network. Furthermore, they offer free decryption of two small files (not exceeding 1Mb). If the victims don't comply, the hackers are threatening that they will attack again.
As always, we advise against contacting the criminals and paying the ransom. There are other ways to restore data. The report indicates[1] that companies who didn't pay the ransom and focused on rebuilding and data recovery spent twice as less than those who complied with the extortion demands.
Victims should remove LAZPARKING ransomware from their infected devices with the help of professional anti-malware software like SpyHunter 5Combo Cleaner or Malwarebytes. These kinds of applications are a must these days because ransomware attacks and malware, in general, aren't going anywhere soon.
After LAZPARKING ransomware removal, the cyberattack victims should take care of their system wellbeing. Commonly malware corrupts and modifies system registry and other essential system files. That could lead to computers exhibiting abnormal behavior. To reverse it, consider using the FortectIntego system repair software.
Message from creators of the LAZPARKING virus to their victims:
Hello!
Your network is penetrated.Forced shutdown of devices can lead to the loss of all data. Do not forcibly disconnect storage volumes from hosts,
interrupt process and restart. Damaged information cannot be recovered.All data is properly protected against unauthorized access by steady encryption technology.
We have downloaded essential data of company:
HR files.
Personal data of employees. Like background checks,ssn,account#,signatures.
Files of ~4000 employees from folder Departmental Shares\CTOPS\Admin\Employee Document Folder (Scan)
Payroll files like tax reports with personal info.
SQL database dumps. For example, 400k records of customers with name,address,email,credit card data from LAZPARIS server.
Marketing data, for example email lists for MailChimp.
Financial, corp accounting data.
…In case if you refuse to cooperate with us, all essential data will be published at forums. Full details and proofs will be
provided in case of contacting us by following emails.jorge.smith@mailfence.com
finbdodscokpd@privatemail.com
It's just a business.
We can help you to quickly recover all your files.
We will explain what kind of vulnerability was used to hack your network.
If you will not cooperate with us, you will never know how your network was compromised. We guarantee this will happen again.
We can decrypt 2 small files (up to 1MB) for free. Send files by email.
Register new email account at secure mail service like mailfence, protonmail to be sure that outgoing email not blocked by spam filter.
Don't use gmail!.WARNING!
Don't report to police. They will suspend financial activity of company and negotiation process.
Dodging ransomware on the world wide web
From annoying adware to perilous trojan horses, the internet is crammed with different kinds all malware,[2] just sitting there in the dark and waiting for oblivious computer users to download it. Different malware is spread in different ways, but ransomware is mainly distributed with the help of spam emails and torrent sites.
Hackers sent out thousands of spam emails each day. These could look like legitimate emails from banks, shipping companies, healthcare institutions, etc. Please don't rush into opening any hyperlinks or attachments. Look through the email, and search for grammatical mistakes or any other irregularities. If the email looks suspicious just delete it and forget about it.
Torrent websites are one of the favorite places for cybercriminals to hide their creations. They name malware as something that would catch the eye of an everyday computer user and upload it. Then they wait for the soon-to-be victim to download, let's say, the latest pirated software or a new game crack. Please don't visit these sites because they are riddled with all kinds of malware.
Using anti-malware software for LAZPARKING ransomware removal
All malware, no matter if it's just annoying or severe, has to be eradicated immediately. The same rule applies to LAZPARKING virus – it must be deleted as soon as it's detected or at the first sight of a ransom demanding note.
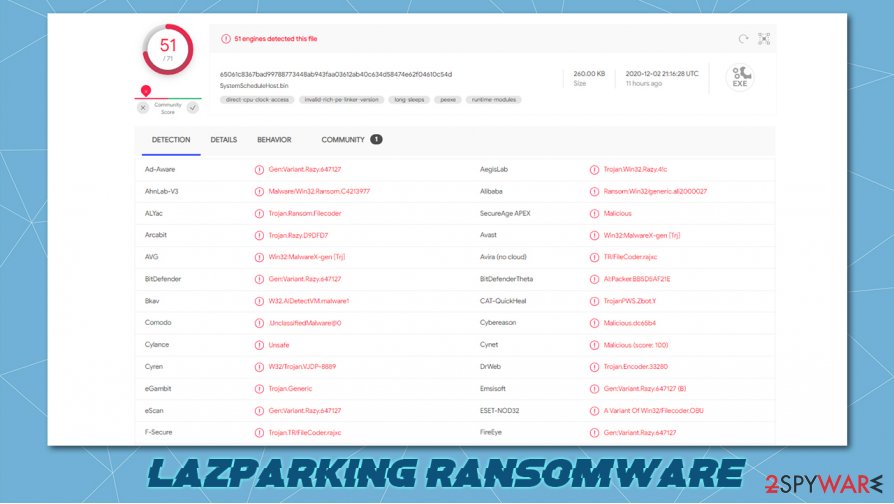
To remove LAZPARKING ransomware, experts[3] suggest using time-proven antimalware software like SpyHunter 5Combo Cleaner and Malwarebytes. These apps should be powerful enough to take care of all the dirty business, as manual ransomware removal is a lengthy and challenging process.
Malware, especially ransomware, changes the system registry and other core system settings to help it thrive. These alterations might slow down your device and exhibit all sorts of abnormal behavior. To restore your computer to a pre-contamination phase (i.e., prior to LAZPARKING ransomware attack), we recommend using the FortectIntego tool.
Getting rid of LAZPARKING virus. Follow these steps
Manual removal using Safe Mode
Safe Mode with Networking might be able to help you with the virus elimination
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove LAZPARKING using System Restore
You can attempt using System Restore,
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of LAZPARKING. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove LAZPARKING from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.If your files are encrypted by LAZPARKING, you can use several methods to restore them:
Data Recovery Pro – a tool for file recovery
This app might be able to get some of your lost files back.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by LAZPARKING ransomware;
- Restore them.
Using Windows Previous Version feature for data recovery
If System Restore was enabled and not deleted, then with this Windows OS feature users might be able to recover files one at a time.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Shadow Explorer – a powerful recovery tool
Use this app to recover data if the Shadow Volume Copies weren't removed by the infection.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
No decryption is currently available
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from LAZPARKING and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting ransomware
Stream videos without limitations, no matter where you are
There are multiple parties that could find out almost anything about you by checking your online activity. While this is highly unlikely, advertisers and tech companies are constantly tracking you online. The first step to privacy should be a secure browser that focuses on tracker reduction to a minimum.
Even if you employ a secure browser, you will not be able to access websites that are restricted due to local government laws or other reasons. In other words, you may not be able to stream Disney+ or US-based Netflix in some countries. To bypass these restrictions, you can employ a powerful Private Internet Access VPN, which provides dedicated servers for torrenting and streaming, not slowing you down in the process.
Data backups are important – recover your lost files
Ransomware is one of the biggest threats to personal data. Once it is executed on a machine, it launches a sophisticated encryption algorithm that locks all your files, although it does not destroy them. The most common misconception is that anti-malware software can return files to their previous states. This is not true, however, and data remains locked after the malicious payload is deleted.
While regular data backups are the only secure method to recover your files after a ransomware attack, tools such as Data Recovery Pro can also be effective and restore at least some of your lost data.
- ^ Elizabeth Montalbano. Paying Ransomware Crooks Doubles Clean-up Costs, Report. Threatpost. Security news.
- ^ What is malware?. Quostar. It support, consultancy and security.
- ^ Wubingdu. Wubingdu. Spyware and security news.





















