HSBC virus (Removal Guide) - updated May 2021
HSBC virus Removal Guide
What is HSBC virus?
HSBC virus a malicious email campaign spreading known trojans like TrickBot

HSBC virus is spam which is spread via misleading email messages that claim to be from HSBC Bank. There are different types of scamming letters and most of them claim that the payment process has failed and to fix things users need to download the attached file or provide some particular information.
These malicious documents can come in names such as BACs.doc, Incoming_CHAPS_Form.doc, report11052018.xls, Paymentreceipt.xlsx, swift_274456.iso which includes swift_274456.exe. For example, the BACs.doc delivers TrickBot trojan and the swift_274456.iso payload carries NanoCore RAT which can initiate malicious activities when planted on a machine.
| Name | HSBC email virus |
|---|---|
| Type | Spam tool/malware/trojan |
| Danger | This spam campaign distributes Trojan viruses via dangerous attachments |
| Related files | BACs.doc, Incoming_CHAPS_Form.doc, report11052018.xls, Paymentreceipt.xlsx, swift_274456.iso which includes swift_274456.exe |
| Malware | TrickBot and NanoCore RAT |
| Detection | Use antivirus for completing a full malware scan |
| Disabling | Check at the bottom of the article for system reboot options |
| PC repair | Run a tool like FortectIntego that can repair affected files on the system |
HSBC email virus can come in more than one message as there are several examples sent by the cybercriminals who are trying to misuse the bank's official name. There have been numerous reports about scams spreading via the HSBC name. One researcher discovered the illegitimacy of a scam message by highlighting the entire text and spotting the in-betweens (the hidden words).[1]
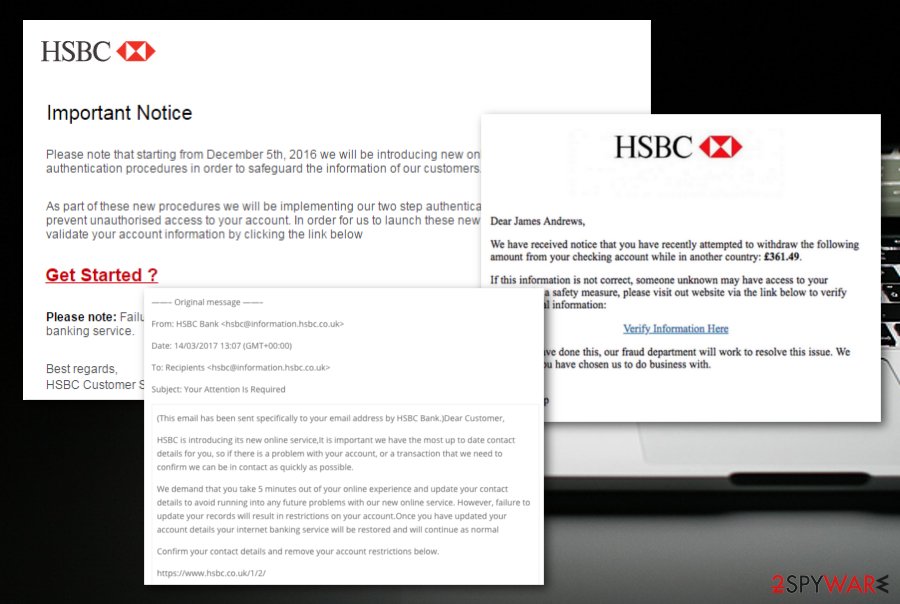
Another spam message reached the surface as an Importance Notice from HSBC. The email urged users to validate account details by clicking a hyperlink below that asked: “Get Started?”. Researchers discovered that after clicking the given link, you are taken to a fake website named wleifhvosidjv.com that imitates an HSBC form.[2] This type of virus asks to log into personal banking through which credentials might be stolen.
Pyranet IT solutions have also released a report in the past about an ongoing email virus spam campaign and described in details all the steps on how not to mix fake messages with original ones. One of the ways is to identify the domain the message takes you to. Anything not related to the official website needs to be marked as suspicious and should be closed immediately.[3]

HSBC virus even has been spread via SMS. The message claims that your account has been locked and to unlock it, you should click on the reactivation hyperlink.[4] Be aware as this is another type of spam content. Erase these types of messages and avoid clicking on the link as you might be redirected somewhere malicious or asked to enter your credentials/personal information.
As long as email virus has numerous variants, you can receive any type of email. One of the most popular messages that might be sent by hackers for malicious purposes looks like this:
Subject: Important : Troubles processing BACs payment
Good Morning,
We’re having troubles processing your request, we encountered an error processing your BACs payment.
What we need you to do
1. The documents are delivered through secure email via an attached file from HSBC. Please be aware this may be delivered to the spam folder.
2. When you open the document a message will appear saying the document requires phone verification. When you click the Send Code button, a code will be sent to your mobile phone.
3. Key that code in to the Code box on screen and select OK. You will now be able to complete the fields in the document as required.
4. Please note that the signature you upload needs to be a clear, current version of your standard signature which once added to the bank mandate can be used to authorise such account transactions as the paying away of funds.
5. Please ensure when you complete the form, that full names including any middle names are included.
6. When the final signatory has completed and signed the documents they will then be returned to me via secure email.
Yours sincerely
James HolandTransaction Processing Specialist | Operations BACs, Faster Payments, CDD |
Email: James.Holand@hsbc.co.uk
If you ever spot some spam related to the organization, you need to remove virus from your email box immediately. Also, you should use an anti-malware tool such as SpyHunter 5Combo Cleaner or Malwarebytes to scan the entire system for possible malware traces. You need to still be careful as some suspicious threats might have entered your system through the email spam. FortectIntego can help with the leftovers and even damage of the system data.
HSBC virus removal is also a necessity if you want to avoid possible trojan infections that these messages are capable of bringing. If at any case a dangerous virus has found a way to your system, you should look at the end of the article and discover ways how to disable malicious processes on your infected machine.
Although this email virus is just a spam campaign and if you ignore its messages, you should not experience any damage, but by entering its links or downloading specific attachments you might have to face very dangerous consequences. This might relate to permanent data loss, exposure of personal information, and swindle of banking details.
The operation process of Trojan viruses
As you already know, email virus is capable of distributing trojan infections. These infectious pieces of software enter the system unknowingly through malicious attachments or hyperlinks. Once installed on the machine/device, alterings of system settings, registries, and files begin.
Some trojans are capable of providing remote access to the criminals that have created them. This is one of the most dangerous activities as by gaining remote access, the crook can modify anything in the victim's computer or steal any type of personal information. Such Trojan viruses are also known as RATs.[5]
Besides data collecting activities, trojans that get delivered by virus or similar spam campaigns are sadly-expected to overuse system resources. These symptoms show up in the Central Processing Unit and Graphics Processing Unit. If the power reaches 90% and more, such intense work can be very harmful to the computer.
Malware distributes through spam campaigns all the time
According to computer specialists from Virusai.lt,[6] various malware forms, including Trojan viruses, ransomware, botnets, cryptocurrency miners, and similar, find their way into the system silently. This mostly happens when the potential victim opens a spam message and attachment or file that comes with it.
Always be careful while managing your inbox. Messages which fall straight into the spam section need to be eliminated without any doubts. Furthermore, always check for possible grammar mistakes, identify the sender, and any hyperlinks if there are some. For file scanning, use a reliable anti-malware program.
Delete email virus before any problems occur
If you have been dealing with this spam campaign, you need to make sure that virus removal is performed before anything bad happens. Use automatical software for the process and also download a scanning tool such as SpyHunter 5Combo Cleaner, or Malwarebytes to find out if your computer system is clean and safe from malware after all.
However, if you remove virus and some malicious activities do reach the surface, you can disable all threatening processes by following the below-provided boot options. You might want to try to repair issues with system performance by running a tool like FortectIntego. System Restore and Safe Mode with Networking are the methods that might help you to deactivate malicious components and stop them from performing further tasks.
Getting rid of HSBC virus. Follow these steps
Manual removal using Safe Mode
If some type of malware has infiltrated your computer system, perform the below-given guidelines to activate Safe Mode with Networking and disable the threat:
Important! →
Manual removal guide might be too complicated for regular computer users. It requires advanced IT knowledge to be performed correctly (if vital system files are removed or damaged, it might result in full Windows compromise), and it also might take hours to complete. Therefore, we highly advise using the automatic method provided above instead.
Step 1. Access Safe Mode with Networking
Manual malware removal should be best performed in the Safe Mode environment.
Windows 7 / Vista / XP
- Click Start > Shutdown > Restart > OK.
- When your computer becomes active, start pressing F8 button (if that does not work, try F2, F12, Del, etc. – it all depends on your motherboard model) multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list.

Windows 10 / Windows 8
- Right-click on Start button and select Settings.

- Scroll down to pick Update & Security.

- On the left side of the window, pick Recovery.
- Now scroll down to find Advanced Startup section.
- Click Restart now.

- Select Troubleshoot.

- Go to Advanced options.

- Select Startup Settings.

- Press Restart.
- Now press 5 or click 5) Enable Safe Mode with Networking.

Step 2. Shut down suspicious processes
Windows Task Manager is a useful tool that shows all the processes running in the background. If malware is running a process, you need to shut it down:
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Click on More details.

- Scroll down to Background processes section, and look for anything suspicious.
- Right-click and select Open file location.

- Go back to the process, right-click and pick End Task.

- Delete the contents of the malicious folder.
Step 3. Check program Startup
- Press Ctrl + Shift + Esc on your keyboard to open Windows Task Manager.
- Go to Startup tab.
- Right-click on the suspicious program and pick Disable.

Step 4. Delete virus files
Malware-related files can be found in various places within your computer. Here are instructions that could help you find them:
- Type in Disk Cleanup in Windows search and press Enter.

- Select the drive you want to clean (C: is your main drive by default and is likely to be the one that has malicious files in).
- Scroll through the Files to delete list and select the following:
Temporary Internet Files
Downloads
Recycle Bin
Temporary files - Pick Clean up system files.

- You can also look for other malicious files hidden in the following folders (type these entries in Windows Search and press Enter):
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
After you are finished, reboot the PC in normal mode.
Remove HSBC using System Restore
Using System Restore on your infected computer might allow you to stop various malicious processes from being carried on further:
-
Step 1: Reboot your computer to Safe Mode with Command Prompt
Windows 7 / Vista / XP- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
-
Select Command Prompt from the list

Windows 10 / Windows 8- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
-
Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Step 2: Restore your system files and settings
-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of HSBC. After doing that, click Next.


-
Now click Yes to start system restore.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from HSBC and other ransomwares, use a reputable anti-spyware, such as FortectIntego, SpyHunter 5Combo Cleaner or Malwarebytes
How to prevent from getting malware
Choose a proper web browser and improve your safety with a VPN tool
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can't grant full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features. However, if you want true anonymity, we suggest you employ a powerful Private Internet Access VPN – it can encrypt all the traffic that comes and goes out of your computer, preventing tracking completely.
Lost your files? Use data recovery software
While some files located on any computer are replaceable or useless, others can be extremely valuable. Family photos, work documents, school projects – these are types of files that we don't want to lose. Unfortunately, there are many ways how unexpected data loss can occur: power cuts, Blue Screen of Death errors, hardware failures, crypto-malware attack, or even accidental deletion.
To ensure that all the files remain intact, you should prepare regular data backups. You can choose cloud-based or physical copies you could restore from later in case of a disaster. If your backups were lost as well or you never bothered to prepare any, Data Recovery Pro can be your only hope to retrieve your invaluable files.
- ^ James Andrews. Clever HSBC scam that made one major mistake – how I spotted it. Mirror. Independent news source.
- ^ HSBC Phishing Email Scam. This Interests Me.
- ^ Your Attention Is Required, SCAM email from HSBC Bank. Pyranet IT solutions.
- ^ Geraldine Strawbridge. Scam of the Week - HSBC Customers Targeted with Phishing Texts. Meta Compliance. Blog.
- ^ Andrew Heizman. What is RAT Malware, and Why Is It So Dangerous?. How To Geek.
- ^ Virusai.lt. Virusai. Spyware and security news.





















